WithSecure™ Elements EPP for Computers Premium: Cyber Threats Resolved!

The Need for Cybersecurity in Bahrain:
In today’s ever-evolving digital landscape, cybersecurity is a top priority for businesses and individuals in Bahrain. Recognizing this critical need, Nexcel, a leading provider of cutting-edge technology solutions in Bahrain, is proud to announce a strategic collaboration with WithSecure, a global cybersecurity powerhouse. This partnership merges WithSecure’s advanced global cybersecurity solutions with Nexcel’s in-depth understanding of the Bahraini market. By combining forces, we empower businesses and users in Bahrain with the most comprehensive and effective protection available. Through this collaboration, Nexcel and WithSecure aim to revolutionize cybersecurity in Bahrain, fostering a safer and more secure digital environment for all.

Windows protection
Windows, the dominant desktop operating system, is a frequent target for cyberattacks. The rising number of threats, as evidenced by a 6000% increase in ransomware email attacks in 2016 (study reference), underscores the critical need for robust security. WithSecure™ Elements EPP for Computers for Windows addresses this challenge by employing a multi-layered approach. This comprehensive solution leverages advanced technologies like automated patch management, machine learning, and real-time threat intelligence to proactively safeguard your Windows environment.
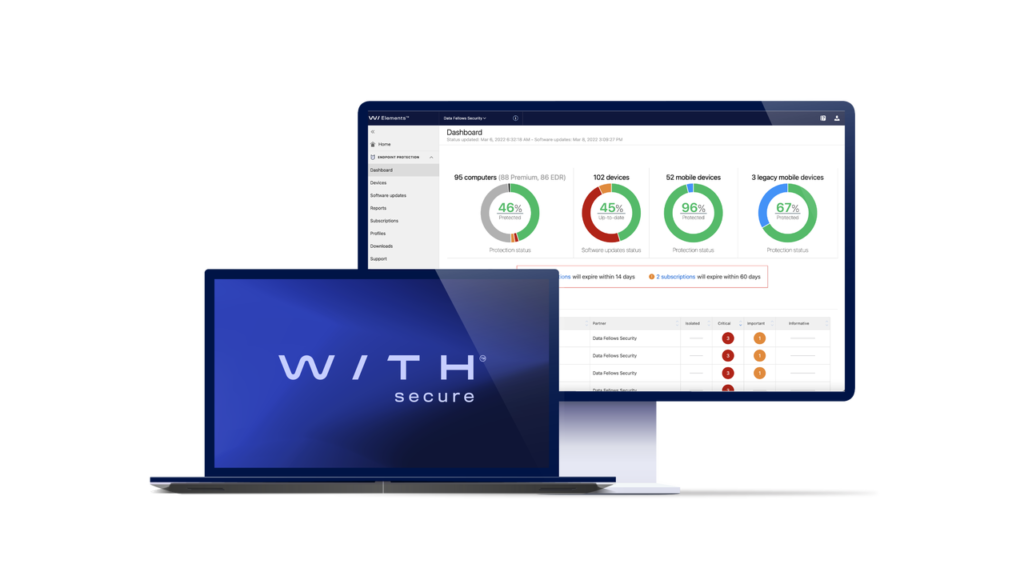
Why WithSecure™ Elements Endpoint Computer Protection for Windows?
Choosing WithSecure Elements EPP Computers for Windows, you get powerful and efficient security that goes far beyond traditional antivirus. It’s a proactive approach to cybersecurity, keeping you a step ahead of actively evolving threats and ensuring the continued safety of your Windows environment.

WithSecure™ EPP Features: A Brief Introduction!
Software Updater: Automated patch management
WithSecure Elements EPP goes beyond endpoint protection by including Software Updater, a seamless and automated patch management solution. This eliminates the need for separate installations of agents, management servers, or consoles, simplifying security management for your Windows environment.
Software Updater plays a vital role in endpoint security. By automatically scanning for missing updates and patching vulnerabilities, it can prevent up to 80% of attacks. This proactive approach strengthens your first line of defense against malicious content.
Software Updater extends beyond the Windows operating system, safeguarding your system by patching vulnerabilities in over 2500 popular third-party applications.
DeepGuard: Heuristic & behavior analysis
WithSecure Elements EPP incorporates DeepGuard, a cutting-edge technology that acts as your final line of defense against even the newest and most sophisticated threats. Unlike traditional antivirus that relies on known threat signatures, DeepGuard focuses on malicious behavior patterns. This allows it to identify and block even zero-day attacks that exploit previously unknown vulnerabilities.
DeepGuard employs a multi-step process to achieve this superior protection:
- Real-time Behavior Monitoring: DeepGuard observes how applications behave on your system, looking for any suspicious actions that could indicate malware.
- Advanced Threat Analysis: When it encounters an unknown or suspicious program, DeepGuard temporarily delays its execution. It then performs a thorough analysis, including checking the file’s reputation, prevalence, and running it in a safe sandbox environment.
- Proactive Threat Interception: Based on the analysis, DeepGuard can either allow the program to run safely or block it if it detects malicious behavior, effectively stopping the threat before it can cause any damage.
By combining real-time behavior monitoring with advanced analysis techniques, DeepGuard provides an extra layer of security that safeguards your system against even the most evasive threats. (For more information & functions of DeepGuard checkout the manufacturer’s technical whitepaper)
DataGuard: Protect data against ransomware
WithSecure Elements EPP goes a step further with WithSecure™ DataGuard, a feature designed specifically to combat ransomware attacks. DataGuard identifies and shields your most critical folders, such as Downloads, Documents, and data repositories, with an extra layer of protection.
Here’s how DataGuard strengthens your defenses:
- Advanced Monitoring: It constantly monitors these high-risk folders for suspicious activity, detecting even the newest and most evasive ransomware threats.
- Fortified Protection: DataGuard goes beyond traditional signature-based protection. Its advanced detection logic identifies and blocks malicious applications, even unknown ones, from accessing, modifying, or encrypting your data.
- Ransomware Recovery: In the unfortunate event of a successful ransomware attack, DataGuard can be instrumental in recovering your data. Since it prevents encryption within protected folders, you may still have access to your critical files.
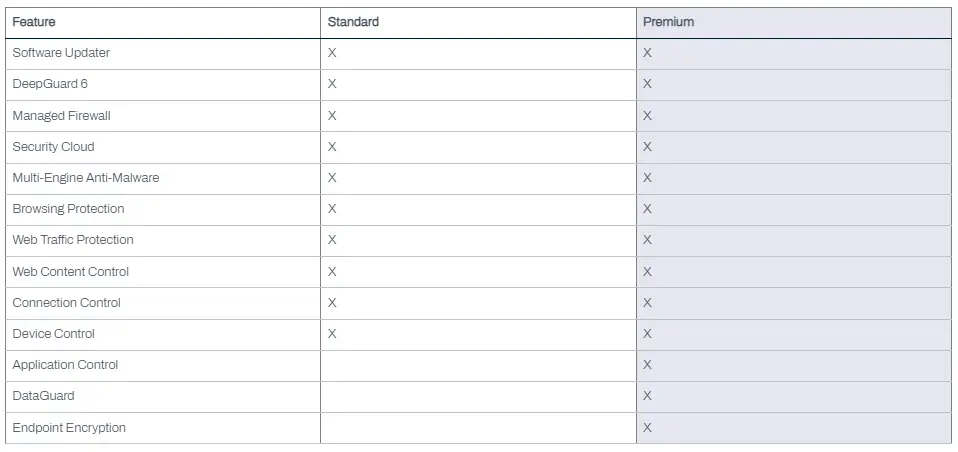
DataGuard is available exclusively in WithSecure Elements EPP for Computers Premium, providing an essential layer of security against today’s ever-evolving ransomware threats.
Security Cloud: Real-time threat intelligence
WithSecure Elements EPP leverages the power of the cloud with WithSecure™ Security Cloud, our advanced threat analysis system. This cloud-based platform utilizes Big Data, Machine Learning, and a vast network of client systems to provide real-time protection against evolving threats.
Here’s how the WithSecure Security Cloud empowers your defenses:
- Global Threat Intelligence: The Security Cloud gathers real-time threat data from a vast network of protected devices, providing a comprehensive picture of the global threat landscape. This helps to identify new threats as they emerge, often within minutes.
- Rapid Threat Response: Threat intelligence is swiftly analyzed and translated into actionable protection. If DeepGuard detects a zero-day attack, for instance, the information is shared through the Security Cloud, rendering the attack harmless on all protected devices within minutes.
- Continuous Knowledge Base Growth: The Security Cloud constantly learns and evolves, adding new threat data to WithSecure’s extensive knowledge base. This ensures your protection stays current against even the newest threats.
For a deeper dive into the technical specifications and benefits of WithSecure™ Security Cloud, please refer to manufacturer’s technical whitepaper.
Multi-Engine Anti-Malware: Superior malware protection
Surpass traditional antivirus with WithSecure Elements EPP for Computers. The multi-engine security platform takes malware defense to the next level by:
- Unveiling Hidden Threats: It goes beyond signature-based detection, identifying a broader range of malicious patterns and behaviors. This empowers WithSecure Elements EPP to uncover even the newest and most sophisticated malware variants, keeping you safe from unforeseen threats.
- Real-Time Threat Response: Leveraging the power of the WithSecure Security Cloud, the solution delivers real-time lookups, ensuring near-instantaneous protection against emerging threats. This keeps your defenses constantly updated and minimizes the window of vulnerability.
- Lightweight and Powerful: WithSecure Elements EPP maintains a small footprint on your system, ensuring smooth operation without sacrificing security.
- Unmasking Obfuscated Malware: Emulation technology provides an additional layer of security to analyze suspicious files in a safe sandbox environment. This exposes even malware that uses obfuscation techniques to hide its malicious intent.
Through WithSecure Elements EPP, you get comprehensive and proactive protection against today’s ever-evolving malware landscape.
Browsing Protection: Prevent access to malicious sites
WithSecure Elements EPP goes beyond endpoint protection to safeguard you from online threats with Browsing Protection. This proactive security layer acts as a shield, preventing you from unknowingly accessing malicious websites.
Here’s how Browsing Protection keeps you safe:
- Real-Time Threat Detection: Leveraging the power of WithSecure’s Security Cloud, Browsing Protection fetches the latest website reputation data. It analyzes various factors like IP addresses, URL keywords, and even site behavior to identify and block access to malicious websites.
- Phishing Defense: Phishing scams often try to trick you into visiting fake websites that look legitimate. Browsing Protection helps you stay safe by preventing you from accessing these deceptive sites.
- Malicious Link Protection: Emails and online advertisements can sometimes contain links that lead to malicious websites. Browsing Protection identifies these threats and prevents you from clicking them, minimizing your exposure to malware and other online attacks.
- Browser-Agnostic Protection: Unlike some security solutions, Browsing Protection works at the network level, offering comprehensive protection regardless of the web browser you use. This ensures your safety even if you’re not using a company-approved browser.
By proactively blocking access to malicious websites, Browsing Protection significantly reduces your risk of encountering online threats and becoming a victim of cyberattacks.
Web Traffic Protection: Block malicious web content
WithSecure Elements EPP takes your online security a step further with Web Traffic Protection. This advanced feature safeguards you against exploit attempts that leverage commonly used plugins like Java and Flash, which are frequent targets for cyberattacks.
Here’s how Web Traffic Protection strengthens your defenses:
- Real-Time Traffic Monitoring: Web Traffic Protection scans your web traffic in real-time, analyzing it with multiple anti-malware engines and reputation checks. This multi-layered approach ensures even the most sophisticated threats are identified and blocked.
- Exploit Interception: Suspicious websites and unknown sites are automatically blocked from exploiting vulnerabilities in Java and Flash. This significantly reduces your risk of infection from these common attack vectors.
- Granular Control for Administrators: For trusted websites, such as your company intranet, administrators can create exceptions within a “trusted sites list.” This allows access to essential resources while maintaining overall security.
- Advanced Threat Defense: Web Traffic Protection goes beyond traditional protection. It can even detect and block memory-only malware, a particularly challenging type of threat.
By proactively scanning and filtering your web traffic, Web Traffic Protection provides an extra layer of defense, safeguarding you from a wide range of online threats.
Connection Control: Elevated security for vital websites
WithSecure Elements EPP offers advanced protection for business-critical online activities with Connection Control. This feature automatically bolsters security whenever you access websites that require an extra layer of protection, such as company intranets or sensitive cloud services like CRMs.
Here’s how Connection Control safeguards your business data:
- Automatic Security Boost: When accessing high-risk websites, Connection Control seamlessly elevates security for that specific session. This additional protection minimizes the risk of data breaches.
- Focused Isolation: During these secure sessions, Connection Control temporarily blocks network connections to all unknown sites from your device. This prevents malware, like banking trojans, from transmitting confidential business information like user credentials or cloud data to unauthorized individuals.
- Maintaining Productivity: You can still access verified safe websites while Connection Control is active, ensuring minimal disruption to your workflow.
- Dynamic Protection: Connection Control automatically returns to normal security protocols once the secure session ends, offering a balance between security and user experience.
By providing an extra layer of protection for critical online activities, Connection Control safeguards your business data and minimizes the risk of cyberattacks.
Device Control: Access for approved hardware only
WithSecure Elements EPP safeguards your system against threats that can enter through external devices with Device Control. This feature offers comprehensive protection against:
- Malicious Hardware: Device Control can prevent threats from entering your system via USB sticks, CD-ROM drives, and even webcams. This helps to minimize the risk of malware infection and data breaches.
- Data Loss Prevention: In addition to blocking threats, Device Control can also be configured to allow only read-only access for specific devices. This helps to prevent sensitive data from being accidentally or intentionally copied out of your system.
Here are some of the ways Device Control empowers you to customize your security settings:
- Granular Device Management: You can set predefined rules to block entire device classes or allow specific devices while blocking others of the same type. For example, you can disable autorun features for removable drives, completely block certain device types, or grant read-only access to specific USB drives.
- Flexible Policy Creation: This level of control allows you to tailor your security posture to your specific needs, ensuring a balance between comprehensive protection and user experience.
With Device Control, you gain an extra layer of security, safeguarding your system against external threats and data leakage.
Application Control: Prevent applications from executing
WithSecure Elements EPP empowers you to maintain a secure and controlled environment with Application Control. This powerful feature acts as a final line of defense against malicious software, even if it manages to bypass other security layers.
Here’s how Application Control safeguards your organization:
- Comprehensive Threat Prevention: Application Control identifies and controls which applications are allowed to run on your devices. This prevents malicious, illegal, or unauthorized software from executing, mitigating a wide range of security risks.
- Automatic Trust Recognition: Application Control can automatically identify and whitelist trusted, authorized software, streamlining the process and minimizing administrative burden.
- Unwanted Software Blockage: Application Control goes beyond basic malware protection. It can also block unwanted or unauthorized applications, even those that may not be inherently malicious, simplifying your IT management and reducing potential security risks.
- Script Execution Lockdown: You can take control by creating rules that prevent specific applications from running scripts, like PowerShell or Batch scripts. This further minimizes the risk of malicious actors exploiting vulnerabilities.
- Customizable Security: Application Control offers administrators the flexibility to create rules based on various criteria, such as application name, version, or origin. This allows you to tailor your security posture to meet your organization’s specific needs.
By providing a robust layer of application control, WithSecure Elements EPP helps you maintain a secure and controlled IT environment, minimizing the risks associated with unauthorized software and script execution.
Firewall Manager: Better Security and compatibility
WithSecure Elements EPP takes firewall management to the next level, offering a user-friendly experience with uncompromised security. Here’s how it achieves this:
- Streamlined Compatibility: Leveraging the Windows rule engine ensures seamless compatibility with your existing applications and appliances. This eliminates potential conflicts and simplifies security management.
- Advanced Threat Protection: WithSecure goes beyond basic Windows firewall functionality. It adds a comprehensive layer of expert rules specifically designed to combat advanced threats like ransomware and lateral movement within your network.
- Customizable Security: Administrators can extend WithSecure’s built-in ruleset with custom rules to address your organization’s specific needs and vulnerabilities. This allows you to tailor your security posture for optimal protection.
- Network-Specific Profiles: The auto-selection feature simplifies security configuration further. By defining network profiles, you can automatically apply the most appropriate security settings for different network environments, ensuring a balance between protection and user experience.
WithSecure Elements EPP offers a powerful and user-friendly firewall solution that delivers robust protection without adding complexity to your IT infrastructure.
Book your WithSecure™ Elements EPP for Computers in Standard and Premium versions now at Nexcel in Bahrain. Bulk discounts for corporate customers available. Contact us for a Free Demo.


Pingback: Data Recovery in Bahrain - Data Privacy guaranteed
Pingback: Cybersecurity in Bahrain - About Zero Click Exploits
Your article on WithSecure™ Elements Endpoint Protection highlights essential features for robust cybersecurity in Bahrain. The integration of DeepGuard for advanced threat analysis and Data Guard for ransomware protection is commendable, offering proactive defense against evolving threats. Emphasizing automated patch management through Software Updater and real-time threat intelligence via Security Cloud ensures comprehensive security for Windows environments. For businesses in Bahrain, these features are crucial, enhancing overall digital safety. Implementing these tools can significantly mitigate cybersecurity risks, safeguarding critical data and systems effectively in today’s complex threat landscape thanks.
Gary
Thanks, appreciate your feedback!